Pharma marketing teams are under growing pressure to personalize HCP and patient engagement while reducing privacy risk.
The challenge is that US healthcare marketing privacy is not governed by one rule; it is shaped by the HIPAA Privacy Rule, state privacy laws, FTC enforcement, and platform-level data restrictions.
This guide is for US pharma brand teams, omnichannel leads, commercial ops, marketing ops, CRM owners, and agency partners who orchestrate journeys across web, media, CRM, hubs, and measurement.
You’ll learn what “changed” heading into 2026 (practically, not hype), how HIPAA applies to common marketing use cases, and what to implement next to reduce friction while improving measurable outcomes.
What changed heading into 2026 (and why it matters for marketers)
There was not a single “new HIPAA law in 2026” that suddenly rewrote pharma marketing, but the operational reality changed because enforcement, consumer expectations, and technical controls tightened. In practice, teams are being forced to prove data provenance, consent/authorization status, and vendor controls across every touchpoint in an omnichannel journey.

First, health data advertising and tracking remains under intense scrutiny from the FTC Health Breach Notification Rule and FTC enforcement actions alleging that certain tracking practices can constitute unauthorized disclosure of health data.
Even when HIPAA does not apply, the FTC can still enforce against unfair or deceptive practices under Section 5 of the FTC Act.
Second, HIPAA’s “marketing” and authorization requirements continue to be a frequent point of misunderstanding, especially when brand teams try to reuse “consent” language from consumer privacy programs. Under the HIPAA Privacy Rule definition of “marketing” (45 CFR 164.501), some communications require an authorization and some do not, depending on purpose and whether remuneration is involved.
Third, state privacy laws expanded and matured, increasing the odds that a pharma program touches “sensitive data” obligations even outside HIPAA contexts. Many programs now need a dual-lens approach: HIPAA where it applies, and state consumer privacy requirements such as the California Consumer Privacy Act (CCPA) as amended by CPRA and state-level health data laws like Washington’s My Health My Data Act.
HIPAA basics for pharma marketers (what HIPAA does and does not cover)
HIPAA applies to covered entities (health plans, many providers, and clearinghouses) and their business associates (vendors handling protected health information on their behalf). Most pharma manufacturers are not covered entities simply by being manufacturers, but many pharma marketing workflows involve PHI flowing from covered entities (for example, patient support programs administered with providers, specialty pharmacy workflows, or hub services), which can bring HIPAA obligations into the operating model.
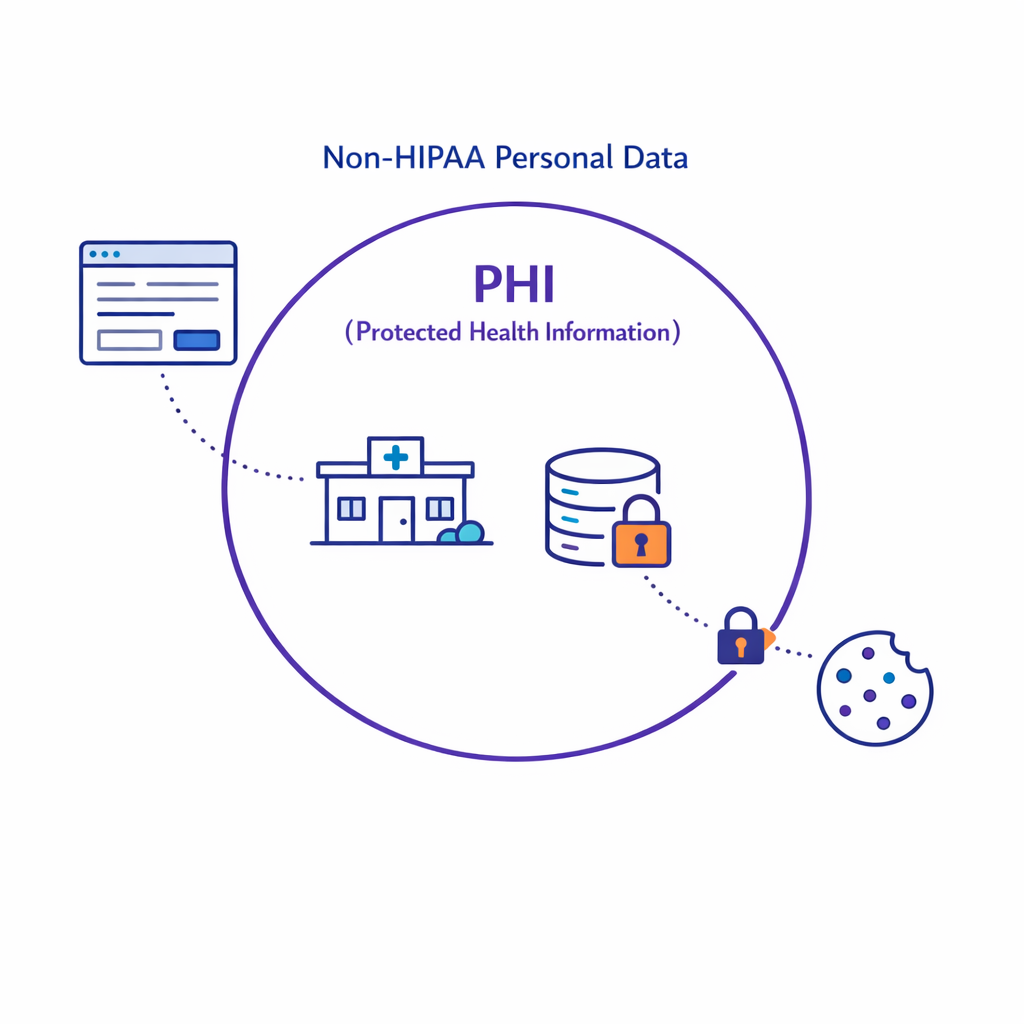
HIPAA protects protected health information (PHI), generally meaning individually identifiable health information held or transmitted by a covered entity or business associate.
This is different from “health-related data” collected directly by a brand website; that data may still be regulated under state privacy laws or FTC standards, even if it is not HIPAA PHI.
Marketers should also distinguish HIPAA from FDA/OPDP promotional rules. The FDA regulates prescription drug promotion and labeling, with key principles for advertising and promotional labeling described in FDA resources such as Prescription Drug Advertising. Privacy and promotion intersect in areas like patient testimonials, intake forms, and patient support enrollment, but they are governed by different frameworks.
When marketing needs HIPAA authorization (and when it doesn’t)
HIPAA often turns into a bottleneck because teams treat all outreach as “marketing” or assume all patient communications are allowed. HIPAA is more specific: whether a communication is “marketing” depends on purpose, and whether it requires authorization depends on the scenario and any financial remuneration.
What HIPAA calls “marketing”
Under the definition of “marketing” at 45 CFR 164.501, a communication encouraging recipients to purchase or use a product or service is generally marketing, but there are important carve-outs (for example, certain treatment and health care operations communications).
The same section also addresses the role of financial remuneration, which can trigger authorization requirements in contexts that might otherwise be permissible.
What a valid HIPAA authorization must include (45 CFR 164.508)
When authorization is required, the form and content matter. The HIPAA authorization requirements in 45 CFR 164.508 specify core elements such as a description of the information to be used or disclosed, who may disclose and receive it, purpose, expiration, and signature requirements, along with required statements like the right to revoke and potential for re-disclosure.
Teams that are collecting authorizations digitally should also ensure their e-sign process is defensible and retained as part of the compliance record.
HIPAA does not prescribe a single technology, but it does require that covered entities maintain required documentation for a defined period under 45 CFR 164.530(j) documentation retention.

Compound authorizations and “bundling” pitfalls
A common marketing ops mistake is bundling permissions together in a way that violates HIPAA’s conditions for certain authorizations. HIPAA places limits on combining authorizations for different purposes and has specific rules for research-related authorizations, including requirements tied to compound authorizations under 45 CFR 164.508.
If your program touches clinical research or observational studies, coordinate early with privacy counsel and the IRB, because HIPAA authorization intersects with the Common Rule (45 CFR 46) for human subjects research in many institutional contexts.
De-identification, limited data sets, and what marketers get wrong
Many teams say “it’s de-identified” when they really mean “we removed obvious identifiers.” HIPAA is stricter and offers two defined methods for de-identification: Safe Harbor and Expert Determination. If you cannot clearly explain which method you used and how, you should assume the data may still be PHI when handled by a covered entity or business associate.
A useful middle ground is a limited data set, which can include certain fields while excluding direct identifiers, but it requires a Data Use Agreement under 45 CFR 164.514(e).
Limited data sets are often practical for analytics and measurement, but they are not a free pass for ad targeting, and they still require strict contractual controls.
Also remember that “anonymous” in consumer ad tech does not necessarily align with HIPAA de-identification. If a dataset can reasonably be linked back to a person, it may still be personal data under state law, and regulators have signaled concern about re-identification risk in broader privacy enforcement, including FTC privacy guidance emphasizing privacy and data security expectations.
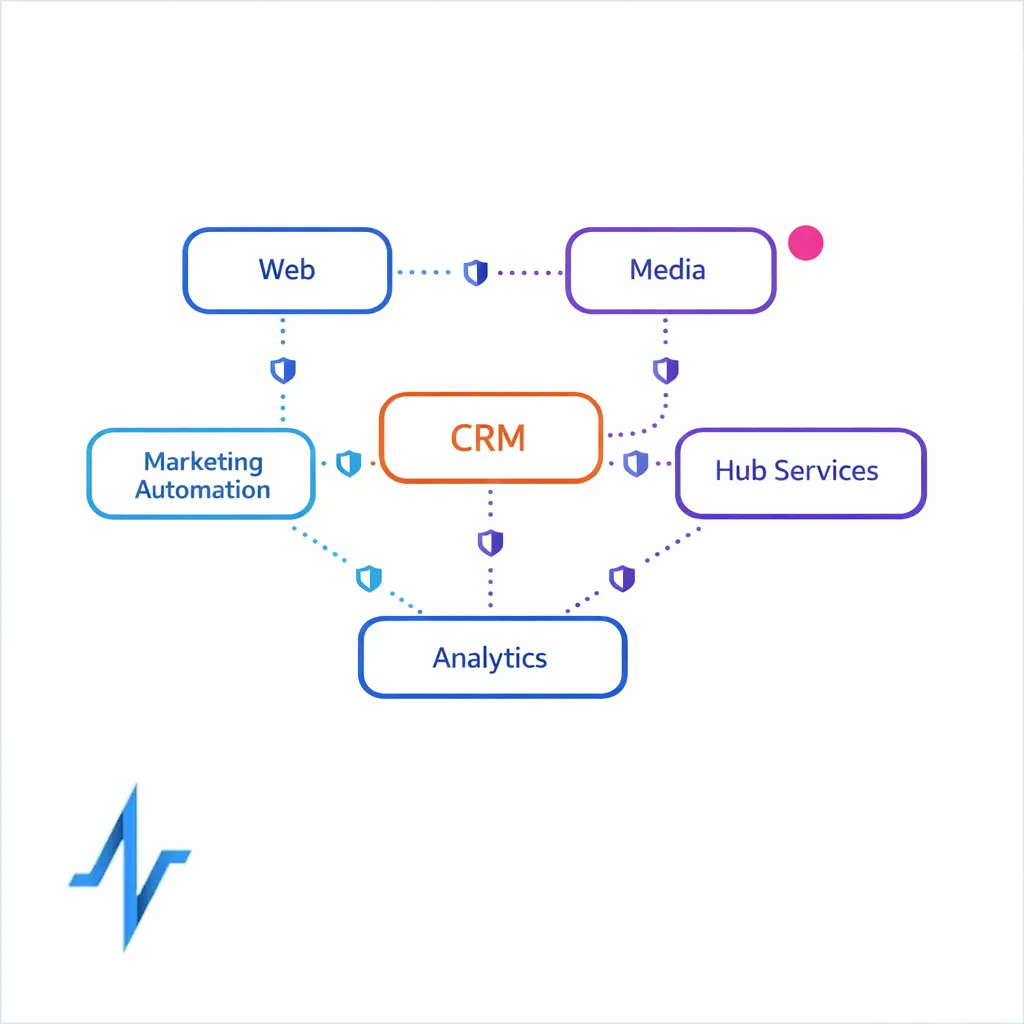
Key pharma marketing workflows: where privacy risk shows up
HIPAA and health data privacy risk tends to concentrate at handoffs: from web to CRM, from hub to brand, from media to measurement, and from agency to vendor. Mapping the “who touches what” is often more important than debating definitions in the abstract.
Patient education sites and sign-ups
Patient education and enrollment flows can collect sensitive information even before a person becomes a patient in a covered-entity context. If the data is collected by a non-covered entity (for example, a brand-run website), HIPAA may not apply, but state privacy laws may impose requirements around sensitive data, such as notice and opt-out/consent mechanics under frameworks like the CCPA/CPRA.
If a site is operated on behalf of a covered entity or integrated into provider workflows, the same flow may become PHI-handling and trigger HIPAA obligations, including safeguards under the HIPAA Security Rule for electronic PHI.

HCP engagement and field enablement
HCP marketing usually involves professional data, but it can still pull in patient context through referrals, case discussions, or program eligibility checks. Where PHI is involved, use and disclosure must align with permitted purposes under the HIPAA “general rules” for uses and disclosures (45 CFR 164.502) and the minimum necessary standard (45 CFR 164.514(d)) when applicable.
Identity resolution and measurement
Identity resolution is where teams most commonly create unintended linkage risk. If you are combining datasets across channels, ensure you understand whether the identifiers originated from a covered entity/business associate relationship or from consumer contexts, and document the permitted uses accordingly.
HIPAA provides a framework for permissible disclosures and restrictions, but it does not automatically authorize cross-context enrichment for advertising; the boundaries are shaped by the HIPAA Privacy Rule and, outside HIPAA, by state laws and FTC expectations.
For digital measurement, review whether trackers could transmit health-related signals to third parties, because regulators have raised concerns about disclosures via pixels and similar tools in health contexts, including compliance expectations under the FTC Health Breach Notification Rule.
Orchestration across CRM, hub services, and partners
Pharma omnichannel programs typically depend on multiple vendors.
If PHI is handled for a covered entity, HIPAA generally requires a Business Associate Agreement (BAA) with appropriate terms governing uses, disclosures, and safeguards.
Vendor governance should also include operational controls aligned to required safeguards under the HIPAA Security Rule, such as access controls, audit controls, and transmission security, tailored to the system’s actual risk profile.
Common misconceptions that cause compliance and performance problems
Privacy risk and marketing underperformance often come from the same root: unclear data classification and inconsistent permissions. Fixing these misconceptions improves both compliance posture and campaign efficiency.
Misconception: “HIPAA applies to all health data.”
HIPAA applies to PHI held by covered entities and business associates, not every dataset that is health-related.
But non-HIPAA health data may still be regulated by state privacy laws and enforced by the FTC under Section 5.
Misconception: “If it’s de-identified, we can do anything.”
HIPAA only recognizes de-identification under Safe Harbor or Expert Determination, and re-identification risk can create legal and reputational exposure even when teams believe the data is “anonymous.”

Misconception: “Consent equals HIPAA authorization.”
HIPAA authorization has specific required elements under 45 CFR 164.508.
A generic marketing consent checkbox often does not meet HIPAA’s content, revocation, and disclosure requirements.
Misconception: “If a vendor says they’re compliant, we’re covered.”
HIPAA requires documented arrangements like a Business Associate Agreement when appropriate, and security controls aligned to the Security Rule.
“Compliant” claims should be validated through contractual terms, audits, and technical evidence.
Practical guidance: designing HIPAA-aware marketing journeys
High-performing pharma teams treat privacy as a systems design problem. They make permissions machine-readable, constrain data to purpose, and architect partner access so that teams can move fast without repeatedly reinventing compliance reviews.
1) Classify data by source and regulatory context
Start by classifying datasets based on whether they are PHI from a covered entity/business associate context or consumer-collected data outside HIPAA. Your classification should reference HIPAA’s definition of PHI and applicability described in HHS HIPAA Privacy Rule materials and your organization’s actual contractual relationships.
- PHI (HIPAA): data originating from covered-entity workflows or handled under BAA.
- Non-HIPAA personal data: brand-collected data potentially subject to state privacy laws (often sensitive).
- De-identified/limited data set: data processed under HIPAA de-identification or limited data set rules, with documentation.
2) Make authorization status explicit and portable
If a use case requires authorization, store the authorization record and its metadata (scope, purpose, expiration, revocation status) as structured fields. This helps you honor the individual’s rights and reduces downstream ambiguity in orchestration. The “what must be included” baseline is defined in 45 CFR 164.508.
For programs operating with covered entities, ensure your operational processes can implement documentation retention requirements under 45 CFR 164.530(j), including versioning and audit readiness.
3) Apply minimum necessary and purpose limitation to reduce exposure
Even when a use or disclosure is permitted, teams should limit data access to what is required for the task. HIPAA’s minimum necessary standard is a practical design principle for role-based access, segmentation logic, and data exports.
- Segment based on eligibility flags rather than clinical details where possible.
- Use tokenization and keyed identifiers to reduce direct identifier exposure.
- Restrict partner access to the minimum fields needed for their scope of work.
4) Control trackers and third-party disclosures
Implement a disciplined approach to pixels, SDKs, and tag managers on pages that may reveal health interests or program participation. The FTC has emphasized expectations for health data sharing and breach notification applicability through guidance on the Health Breach Notification Rule, which is especially relevant when consumer health apps or similar services are involved.
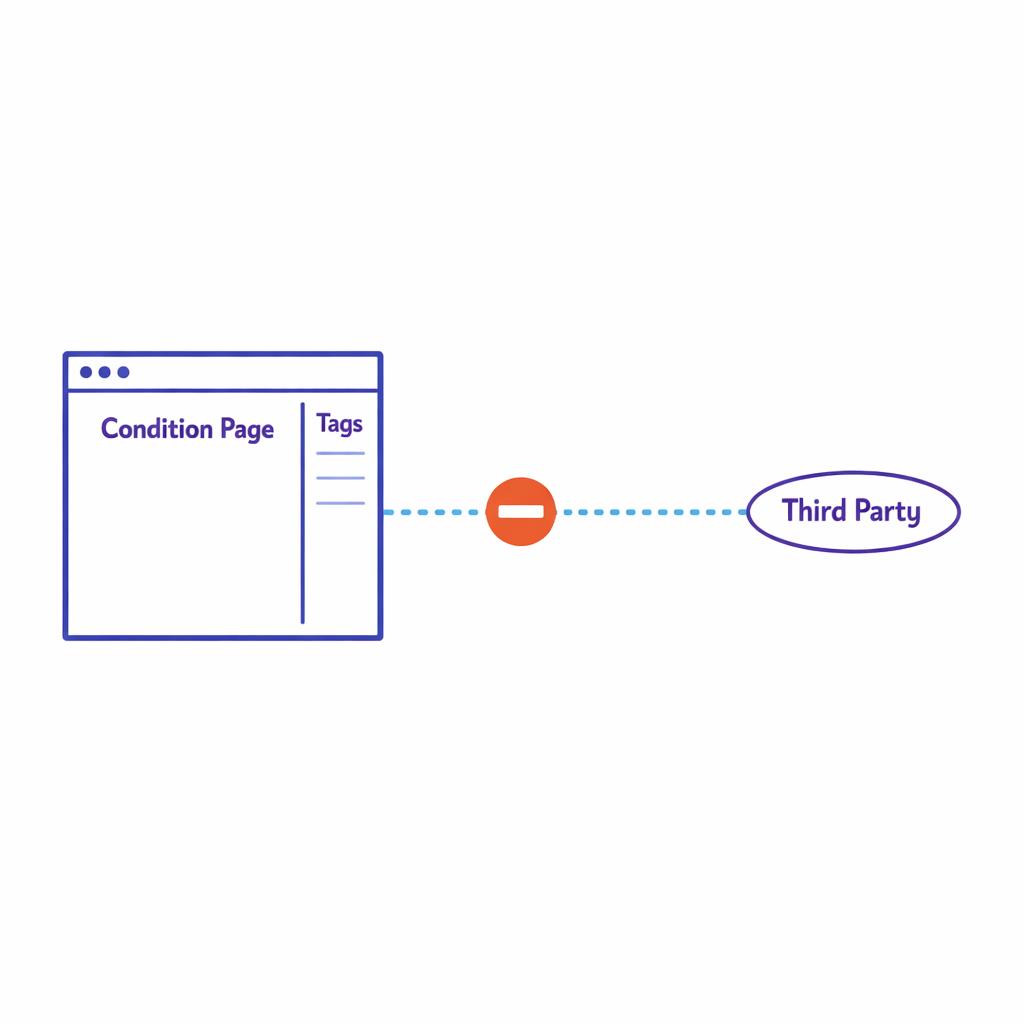
Even if HIPAA is not in scope, avoid sending sensitive signals (for example, condition pages, enrollment confirmation events) to third parties unless your notices and controls clearly support it.
Align disclosures with your privacy representations to avoid FTC risk under Section 5.
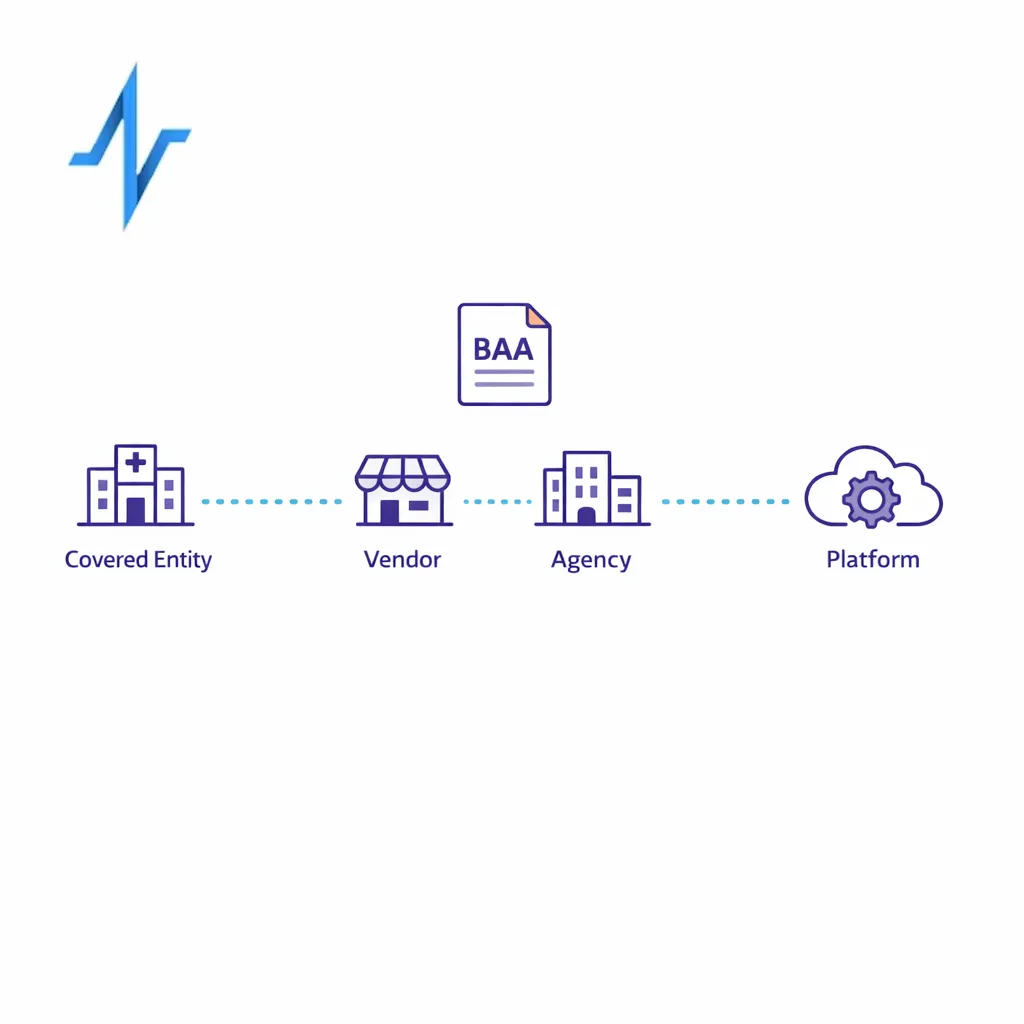
5) Tighten BAAs, DPAs, and partner operating procedures
If a partner is handling PHI on behalf of a covered entity, your contracts should reflect HIPAA business associate obligations and limitations. HHS describes expectations for business associate contracts and other arrangements, and those requirements should map to your actual data flows.
For non-HIPAA personal data, align contract terms to state privacy law obligations and operationalize deletion, access requests, and opt-out logic where required, using baseline obligations described in consumer privacy frameworks like California’s CCPA/CPRA.
What to do next: a 2026-ready compliance and performance checklist
Use this checklist to reduce privacy risk while keeping omnichannel programs measurable and scalable. The goal is to make compliance auditable and automation-friendly, not to slow down launches.
- Map data flows end-to-end across web, CRM, hubs, media, analytics, and agencies, noting where PHI may be created or transmitted under HIPAA Privacy Rule contexts.
- Classify each dataset as PHI, non-HIPAA personal data, de-identified, or limited data set, using HIPAA de-identification guidance and 45 CFR 164.514 for limited data sets.
- Standardize HIPAA authorization templates where needed, ensuring required elements match 45 CFR 164.508 and revocation can be operationalized.
- Build authorization and preference data into your CRM as structured fields so downstream orchestration can enforce scope and expiration.
- Audit pixels/SDKs/tag manager rules on condition- and enrollment-related pages, factoring FTC expectations described in the Health Breach Notification Rule.
- Review BAAs and vendor access where PHI is involved, using HHS guidance on business associates and required contract terms.
- Apply minimum necessary controls to exports, segmentation, and analytics per HIPAA minimum necessary where applicable.
- Align privacy notices to actual practices to reduce FTC risk under Section 5 and to support consumer privacy compliance (for example, CCPA/CPRA).
- Operationalize retention and audit readiness for HIPAA-required documentation under 45 CFR 164.530(j).
How Pulse Health helps teams ship compliant omnichannel programs faster
Compliance is easier when your identity, consent/authorization, and orchestration logic are unified instead of scattered across tools.
Pulse Health is designed to help pharma teams manage patient and HCP engagement workflows with clearer governance over what data is used, for what purpose, and under which permissions, aligned to HIPAA concepts like authorization requirements and operational safeguards expected under the HIPAA Security Rule.
For commercial ops and marketing ops leaders, the practical win is fewer manual reviews and fewer last-minute launch blocks, because teams can standardize how authorization status, preferences, and data classifications flow into activation and measurement. For agencies and partners, the win is clearer boundaries and faster execution with less rework driven by unclear data provenance.
Request a Demo, book a consultation, or explore how it works
If you’re updating your 2026 engagement and measurement stack, consider pressure-testing your journeys against HIPAA authorization requirements, tracker disclosure risk, and partner data handling. Pulse Health can help you instrument permissions-aware orchestration so your teams can personalize responsibly and measure impact with fewer compliance surprises.
- Request a Demo to see how permissions-aware orchestration can work in your current stack.
- Explore Integrations if you need CRM, analytics, hub, or media partners to operate from one permission signal.
- Get the Platform Overview for a practical view of what “compliance by design” looks like for pharma omnichannel.