Privacy in pharma is more than compliance — it’s a competitive advantage. This playbook shows how to build patient trust by: (1) adopting consent-first data and preference management, (2) embedding privacy-by-design across campaigns and your martech stack, and (3) measuring impact without user-level IDs. You’ll also see where Pulse Health integrations (e.g., Pulse Health + Veeva CRM and Pulse Health + OptimizeRx) help orchestrate compliant, high-trust journeys.
Introduction: Why Privacy Is the New Differentiator
Patients now judge pharma brands as much by how they handle data as by what they make. Between signal loss, patchwork privacy laws, and rising expectations, data privacy in pharma marketing is a frontline experience issue — not a back-office checkbox. Teams that make privacy visible — clear consent, transparent purposes, easy preference controls, and consistent follow-through — earn permission, grow first-party data, and strengthen patient trust.
This article delivers a practical, step-by-step playbook:
- How to capture and honor consent
- Apply privacy-by-design to web/email/SMS/media
- Assemble a pragmatic martech blueprint (CMP, server-side tagging, CRM/CDP, clean rooms)
- And measure impact without user-level IDs
We’ll close with a 30/60/90 roadmap and common pitfalls to avoid.
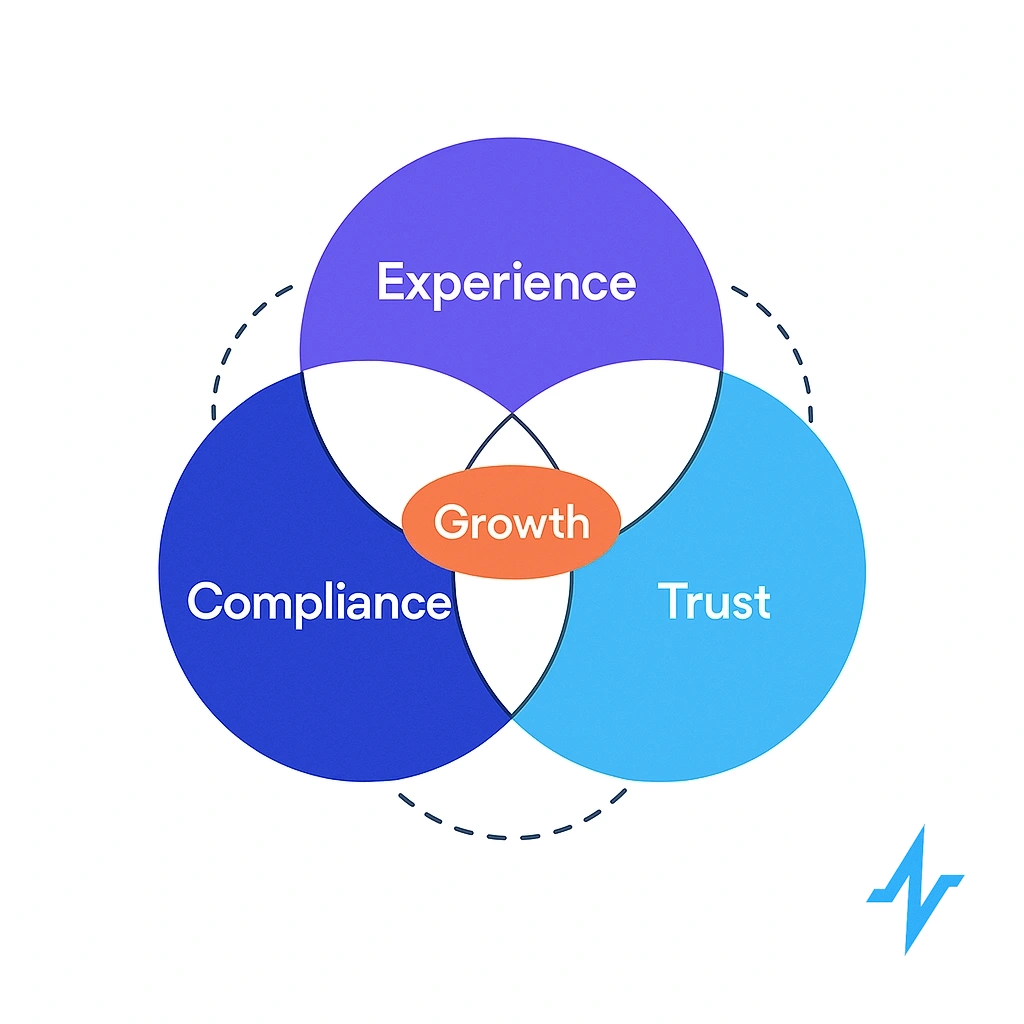
Callout: Treat trust as a KPI. Track opt-in rate, preference selections, unsubscribe sentiment, time-to-fulfill data requests.
Trust, Risk, and the Commercial Stakes
Compliance prevents fines; trust earns permission. When patients understand what you collect and why, more say “yes” to programs, emails, and support resources. That builds richer first-party datasets, reduces media waste, and improves adherence-support engagement — creating a durable growth loop grounded in consent.
Trust Wins (at a glance)
- Higher opt-in rates → more first-party/zero-party data
- Better message relevance → stronger program engagement
- Stronger brand reputation → increased lifetime value
Key Definitions Marketers Must Get Right
Clarity on terminology prevents avoidable risk and over-engineering.
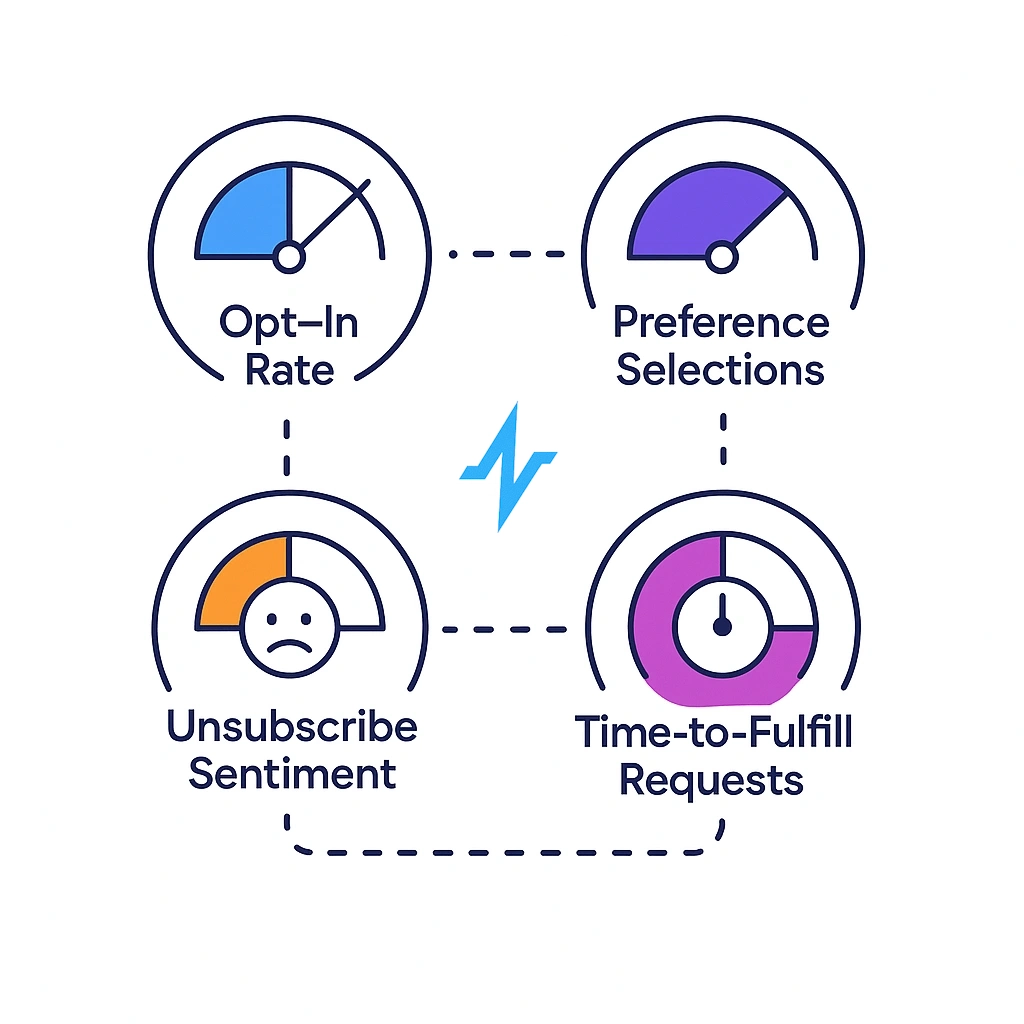
- PHI (Protected Health Information): Identifies an individual and relates to health/healthcare.
- PII (Personally Identifiable Information): Identifies a person, not necessarily health-related.
- De-identified data: Data processed so the individual is not reasonably identifiable.
- Pseudonymized data: Identifiers replaced with tokens but still linkable under controlled conditions.
- Minimum necessary / Data minimization: Collect the least data required for a stated purpose.
Practical takeaway: Keep PHI in controlled systems and, whenever possible, use de-identified or aggregated data for marketing analytics and reporting.
The Regulatory Landscape Marketers Navigate
Use this section to align marketing, data, and legal/MLR on “what matters” operationally.
HIPAA/HITECH & 42 CFR Part 2 (U.S.)
What it means for marketing: Avoid PHI unless you have appropriate consent and safeguards; ensure BAAs where required; secure transmission and storage; be very careful with pixels/tags on condition or support flows.
Common pitfalls:
- Pixels or third-party tags on sensitive pages without consent
- Remarketing audiences inferred from condition content
- Storing consent logs inconsistently across tools
CPRA/CCPA & U.S. State Laws
What it means: Treat certain health-related signals as sensitive; honor do-not-sell/share and Global Privacy Control (GPC); provide accessible opt-out.
Pitfalls: Equating “share” with “sell” incorrectly; ignoring cross-device signals and GPC.
GDPR/UK GDPR & ePrivacy
What it means: Establish a lawful basis — often consent — for processing; use clear cookie consent; maintain records (e.g., DPIAs, DPO where applicable); uphold data subject rights.
Pitfalls: Bundled consent, dark patterns, and inconsistent cookie behavior by region.
Canada (PIPEDA, PHIPA) & Quebec Law 25
What it means: Emphasize express consent and transparency; consider data localization; implement privacy impact assessments (Quebec).
Pitfalls: Using U.S. tools without appropriate assessments/agreements; insufficient disclosure around profiling.
APPI (Japan) & Other Notables (high-level)
What it means: Sensitive personal information rules; cross-border transfer requirements; documentation.
Pulse Health Angle: Pulse Health integrations help teams capture, store, and honor consent consistently across CRM, marketing automation, and engagement tools.
Consent & Preference Management: The New Front Door
Consent is a user experience, not just a banner. Make it clear, contextual, and consistent across web forms, program enrollment, SMS, and email. Capture purpose-based consent, sync it to your CRM/CDP, and enforce it everywhere — journey orchestration, suppression, segmentation, and analytics.
Design principles
- Plain-language microcopy (“why we ask”) near fields
- Layered notices (summary → read more)
- Granular preferences (topics/frequency/channel) vs. binary opt-in
- Time-stamped consent events with audit logs
Pro Tip: Design consent like a product. A/B test language, placement, and friction; measure opt-in rate, completion rate, and complaint rate.
First-Party & Zero-Party Data Strategy
Collect only what you can explain.
Offer clear value (checklists, nurse chats, refill reminders, adherence resources) in exchange for zero-party inputs such as content interests and support preferences.
Use progressive profiling to ask gradually for more detail over time, not on the first touch.
Privacy-Safe Capture Checklist

- Clear purpose + specific benefit
- Minimal fields at first touch (expand later)
- Granular preferences and frequency controls
- Consent logged, synced, and enforced downstream
Data Minimization & De-Identification in Practice
Reduce both risk and operational drag by limiting scope, retention, and access. Keep PHI in controlled systems with role-based access; route analytics using de-identified/aggregated data whenever feasible. Establish retention windows and purge schedules aligned to legal and business needs.
Operational moves
- Maintain a living data inventory and tag registry
- Segment sensitive pages; block/allow tags by page type
- Enforce RBAC; review access quarterly
- Separate PHI workflows from general marketing analytics
Privacy-by-Design for Common Campaign Types
Web & On-Site
- Use server-side tagging to limit data exposure.
- Load only essential third-party scripts; defer or block on sensitive pages unless consented.
- Personalize only with consented signals; provide visible controls.
Email & SMS
- Respect consent flags and preferences across tools.
- Avoid sensitive content without explicit, appropriate consent.
- Implement AE monitoring and routing from replies and landing pages.
Programmatic & Social
- Favor contextual and curated publisher deals over behavioral targeting.
- Avoid sensitive inferences; do not combine PHI with ad identifiers.
- Maintain suppression lists aligned to consent state.
Go/No-Go Checklist Before Launching a Pharma Campaign
- Consent captured and logged
- Sensitive pages free of tracking unless consented
- Server-side tagging plan documente
- Preference flags respected across tools
- AE monitoring route in place
- Suppression rules tested
- Retention timers applied
- Easy opt-down/out present
Your Martech Stack & Governance
A privacy-aware stack aligns capture, enforcement, and measurement.
Core components
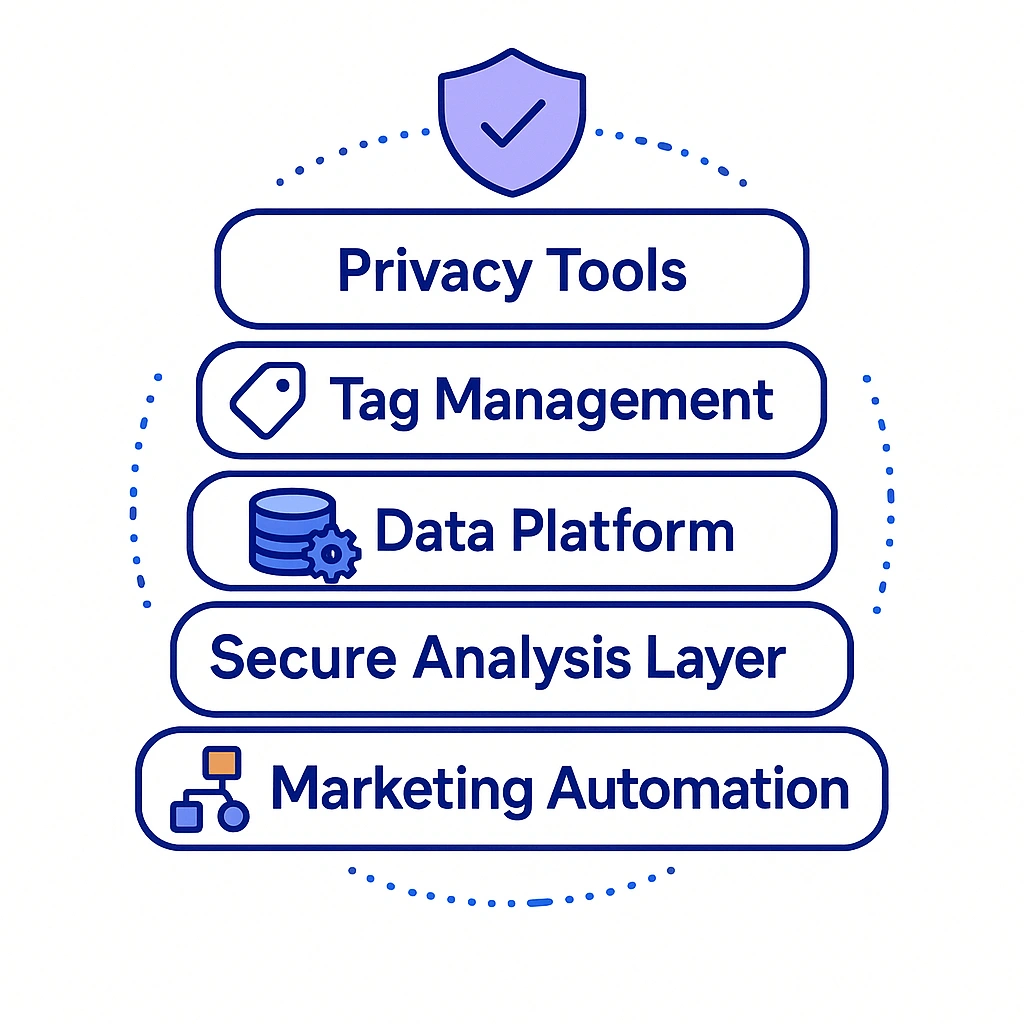
- CMP (Consent Management Platform): Granular purposes, regional behavior, audit logs
- Tag Manager (Server-Side): Route events securely; block by page type
- CRM/CDP (HIPAA-capable): Centralized consent flags; journey orchestration; suppression
- Secure Warehouse/Clean Room: Aggregate analysis; no raw IDs; strict join rules
- Marketing Automation: Enforce preferences; channel-level controls
Governance rituals
- Quarterly tag audits and access reviews (RBAC)
- Vendor risk management: BAAs/DPAs, sub-processors, DPIAs where applicable
- Data lineage and audit trails for consented flows
- Retention enforcement and defensible deletion
Pulse Health Angle: Pulse Health’s integrations reduce swivel-chair work: consent captured once can synchronize across Veeva CRM and engagement tools, minimizing drift and ensuring suppression is honored. See: Pulse Health + Veeva CRM.
Privacy-Safe Targeting & Measurement
Shift from user-level identifiers to contextual, cohort, and publisher-direct methods. Where collaboration is required, use clean rooms with strict controls and only with proper consent. For measurement, rely on aggregate approaches that protect identity.
Targeting approaches
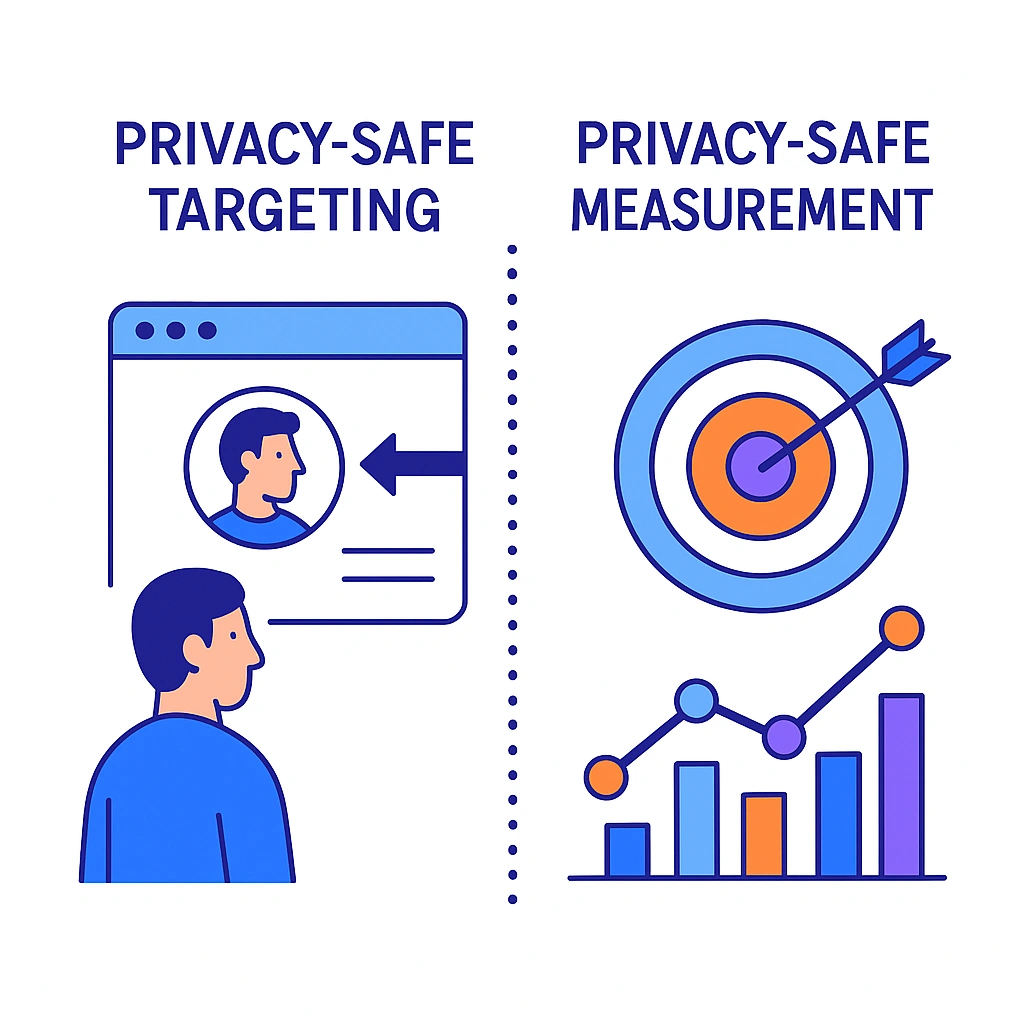
- Contextual placements aligned to condition-agnostic content
- Cohort-level modeling from consented first-party signals
- Publisher direct deals with explicit controls
Measurement without PII
- MMM (media mix modeling) to see macro impact
- Geo-based lift and holdouts for incrementality
- Aggregated conversions and modeled outcomes via server-side pipelines
What We Don’t Do

- Retarget based on condition pages without explicit consent
- Combine PHI with ad IDs
- Sneak pixels onto sensitive flows
Transparency, Messaging & UX Patterns that Earn Trust
Plain-language notices and friendly microcopy boost opt-ins and reduce complaints. Explain why you ask for data and make it easy to opt down or out.
Reusable microcopy (tweak as needed):
“We ask only for information that helps personalize your support. You can change your preferences anytime, and we won’t use your data for unrelated purposes.”
Trust signals near forms
- BAA coverage (where applicable)
- Dedicated privacy contact (e.g., privacy@)
- Link to privacy policy with “last updated” date
- Summary of how to update/delete data
Incident Response, Breach Comms & AE Interlock
Have a simple, rehearsed plan: detect → contain → investigate → notify (if required) → remediate. Coordinate with legal/MLR, and make sure adverse event (AE) capture routes are defined across social and owned channels.
Internal comms template (starter):
“We identified a potential data incident on [date]. We contained access within [timeframe] and are investigating scope and impact. If notification is required, we will contact affected individuals and authorities per policy.”
Don’t forget: Keep AE monitoring rules and escalation paths documented; train community managers and support teams.
30/60/90-Day Implementation Roadmap
Days 0–30: Baseline & Quick Wins
- Tag inventory by page type; block high-risk tags on sensitive pages
- Fix consent UX (copy, placement, region behavior)
- Vendor gap list (BAAs/DPAs; sub-processors)
- Define KPIs: opt-in rate, unsubscribe sentiment, time-to-fulfill requests
Days 31–60: Foundations Live
- Deploy server-side tagging for core events
- Roll out RBAC and quarterly access review cadence
- Launch preference center v1 (topics/frequency/channel)
- Implement retention policy and purge scripts

Days 61–90: Scale & Prove

- Pilot a clean room collaboration with strict joins
- Stand up MMM/geo-lift plan for aggregate measurement
- Formalize quarterly tag audits and consent reconciliation
Common Pitfalls & How to Avoid Them
- Pixels on sensitive pages without consent → Maintain a page-type tag registry and enforce rules.
- Orphaned tags / shadow SaaS → Quarterly tag and vendor audits; approval workflow.


- Consent drift across tools → Centralize consent state in CRM/CDP; automate suppression.
- Over-collection → Short forms first; use progressive profiling later.
Get Started with Pulse Health Today
Privacy-by-design isn’t a constraint — it’s a path to durable performance. Start with clear consent and preferences, tighten your stack and governance, and measure with aggregates. Want a fast path to execution?
Book a privacy audit and see how Pulse Health operationalizes consent across Veeva CRM and your engagement tools.
Schedule a free demo today to learn more.
Frequently Asked Questions
Yes — with appropriate consent and safeguards. Default to de-identified/aggregated data for analytics and avoid combining PHI with ad identifiers.
PHI ties identity to health context; PII identifies a person without necessarily indicating health status.
If analytics/marketing cookies are used, consent is generally required in many jurisdictions; align with local laws and your CMP settings.
They enable aggregate analysis and collaboration without sharing raw IDs; strict access controls and queries reduce re-identification risk.
MMM, geo-lift, server-side aggregated conversions, and modeled outcomes provide decision-quality insights while protecting identity.
Topics, frequency, channels, and an easy way to opt down or out — plus a link to update/delete data.